The Onion Approach to Security
As penetration testers, through the years, we have learned one indisputable fact:
There is no such thing as a 100% secure network.
Sure, we have encountered wide variances in the maturity level and effectiveness of information security programs of various organizations, but we have yet to encounter an organization that is impenetrable – not even close. And while actually implementing an impenetrable network is probably as likely as finding a unicorn, it does not mean we cannot strive for that ideal.
Our collective experience has shown us that, if an attacker is sufficiently motivated and skilled, it is highly likely that attacker will indeed successfully compromise the target organization. That could be your organization’s sensitive data that lands your organization in the news tomorrow as the latest story of yet the next high-profile compromise. Sadly, it is only a matter of time for most organizations. We demonstrate time and again to our clients, that we can indeed get into their networks, and we can indeed gain unauthorized access to their sensitive data. Furthermore, the attack can often go undetected within many of the organizations. The average organization takes over two-hundred days to become aware they’ve been breached and eighty-five percent of the time that occurs from someone outside of the organization… like the FBI knocking on their door.
How do we approach things better?
So, what do we do then? Unfortunately, there is no silver bullet that an organization can procure that will solve all information security problems. Furthermore, there are no security products that are without their own vulnerabilities and weaknesses. If your sales rep for a given security product claims it is the answer to all your security needs, you should politely show him or her the door.
Long gone are the days that one security control was sufficient to properly secure our networks and data. In fact, it is kind of amusing to look back in time to when the prevailing thought, as it regarded information security, was that a firewall was that silver bullet. We would install and configure that shiny new firewall to protect our networks and data from the bad guys. We would even take it a step further and install antivirus software on our systems just on the off-chance something scary slithered past that impenetrable firewall. We would then pat ourselves on the back after a job well done and relax knowing that we were safe from the bad guys. “Yep, we’re good!” The only thing left to do at that point was to figure out where we were going to lunch.
The present day problem of properly securing networks and data has become an enormously larger endeavor. Indeed, it has become a daunting endeavor. It is also a problem that cannot be completely solved unfortunately. There is still hope, however. The problem can certainly be effectively mitigated by implementing a more effective strategy; a strategy which implements the layered approach to information security.
Reintroduction to an age old concept:
One of the most effective strategies an organization can employ to mitigate this problem, and hence effectively strengthen the security posture of the organization, is a Defense in Depth strategy. This is not a new concept by any means. This concept is ubiquitously scattered throughout volumes of information security publications and documentation. Yet, surprisingly, so many organizations dismiss its effectiveness and do not apply enough attention to the proper implementation of this strategy. In fact, some organizations do not implement it at all, believe it or not. As advancements in tools and techniques are made by growing numbers of attackers to circumvent today’s security controls, this strategy becomes more and more important, and relevant, as attacks become more frequent and more sophisticated.
In our line of work the goal is to circumvent security controls. As eluded to before, given sufficient skill and motivation, virtually any single security control can be circumvented, and it is wise to assume this will indeed happen. Any data asset that has but one security control to protect it will almost certainly fall victim to unauthorized access by the bad guys. We, at DirectDefense (the good guys), do this all the time in our day to day work. What makes our job much more difficult (and conversely, your data much more secure) is when several layers of security controls exist to protect the given data asset. The more layers of security that exist to protect the data asset, the lower the probability of compromise of that data asset. Furthermore, the probability of compromise lowers almost exponentially with each additional layer in many cases.
How Bad can it Get:
To illustrate the point we step you through a real-world example of a penetration test which our consultants performed for a client recently. The consultant leveraged a common attack vector which leaves the majority of organizations that we test highly vulnerable to attack; that is, gaining access to the internal network environment by gaining physical access to one of the organization’s facilities. As the old saying in information security goes “Corporate networks and infrastructure are a lot like an M&M: With a hard, crunchy outside and a soft, chewy center”. With that said, let us walk you through an exercise to illustrate the importance of a Defense in Depth strategy.
As part of the engagement performed recently for a client:
- The DirectDefense consultant was tasked to attempt to obtain unauthorized physical access to two targeted facilities at two separate locations.
- If physical access was obtained, the consultant was tasked to attempt to gain access to the internal network environment.
- If access to the internal network was gained, the consultant was tasked to attempt to gain access to the Client’s sensitive data assets. Given the fact that most organizations indeed have a “soft, chewy center”, as they say, this exercise is a great example of why defense in depth and a layered approach to information security is so extremely important.
Below is a description of the events that occurred in 2015 at ClientX’ facility in South Park, CO and Springfield, MI. Although the names and cities have been changed, for the sake of anonymity, the rest of the scenario describes events that occurred during a real penetration test performed by DirectDefense.
Prior to executing the physical penetration tests in South Park, CO and Springfield, MI, the consultant performed some research on the company to devise a plot to socially engineer access into the facilities. The consultant (the attacker) learned via publicly available information that ClientX had recently acquired Company.
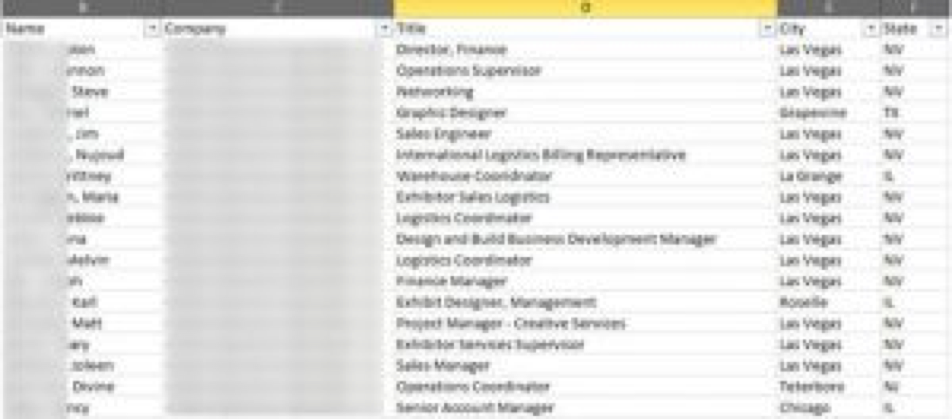
The attacker also gathered information about personnel at ClientX via mining publicly-available resources to use as specific, recognizable people to use to lend credence to the attacker’s bogus plot. The attacker compiled a list of names of people with important titles to lend authority to the mission. The attacker also used ClientX’s telephone call manager system to verify the chosen people were still employed with the organization. The attacker also sent bogus emails to the list of people to see if there were any ‘out-of-office’ replies indicating they may be unavailable. The attacker identified one such person. We will call him “Bob Smith” for anonymity purposes. The attacker chose this person to use in case anyone approached the attacker and asked who authorized the mission. The fact that Bob Smith was unavailable to verify anything would likely allow the bogus plot to remain undetected. The figure below illustrates an excerpt of 297 contacts identified.
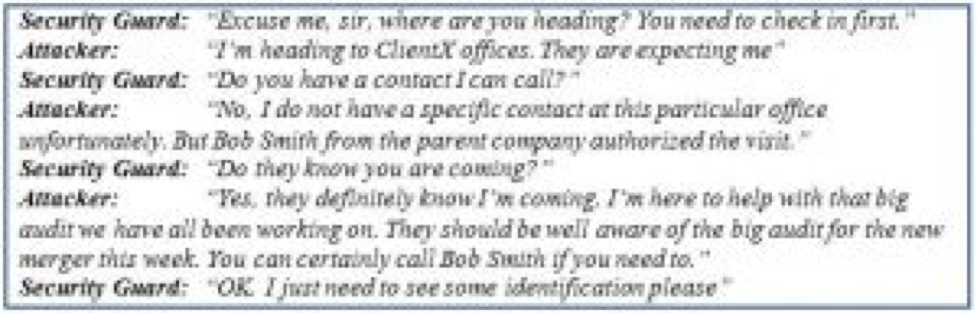
On the morning of the penetration, the attacker entered the lobby of the multi-story building in which the client resided. The attacker then attempted to bypass the security personnel protecting the elevator banks to access the upper floors. The attacker was initially stopped by the security guard. The security guard began asking the attacker questions. The conversation went something like the following dialogue:
The attacker then handed over his driver’s license and the security guard printed up a visitor’s badge, and allowed the attacker to pass and gain access to the elevator bank. The figure below illustrates the badge.

This was the first security control that was circumvented during the penetration test. Although this security control was in place, in the form of a security guard in the lobby, the process to authenticate, and escort visitors, was not followed. This allowed the attacker to circumvent this security control and gain access to the elevator bank leading to ClientX’s floor.
The attacker then rode the elevator to ClientX’s floor and waited for an opportunity to gain unauthorized access into the secured area of the facility. Once an opportunity presented itself, the attacker then tailgated an unsuspecting ClientX employee into the secured area of the facility. Interestingly, the employee was helpful enough to hold the door open to allow access to the secured area of the facility for the attacker. Unfortunately, and alarmingly, based upon our past experience this is a common occurrence when performing physical penetration tests.
It is important to note that another security control was circumvented at this juncture; physical locks securing the doors. Had the organization been implementing ongoing security awareness training for their personnel, the attacker would have likely not been able to bypass the locked doors to gain access to the secure areas of the facility. ClientX personnel did not receive proper security awareness training. This is an important layer of security that was absent.
A common security control that would have aided in the mitigation of the tailgating issue is tailgate protection controls. Had this security control been in place, the attack may have ended at that point. Tailgate protection controls such as half-height turnstiles are a common control organizations employ to effectively mitigate this issue. This particular organization did not implement any other layer of physical security controls other than a locked door at this level of the test. This single security control was easily circumvented.
The attacker then walked around the secured areas of the facility in clear view of ClientX personnel looking for a convenient place to connect to the network. Again, had the organization properly implemented security awareness training as another layer of security the attack would have likely failed at this juncture. The figure below illustrates the attacker walking around the secured areas of the facility while taking photos, without any confrontation from ClientX personnel.

The attacker then identified an unattended cubicle, and connected a laptop to an existing Ethernet cable as illustrated in the figure below.

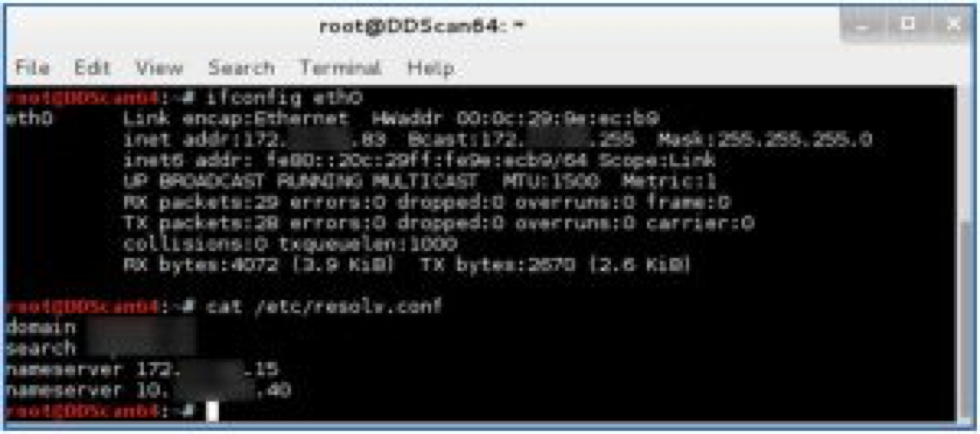
Once physically connected to the network within the acquired cubicle, the attacker received IP address information via Dynamic Host Configuration Protocol (DHCP) as illustrated in the figure below. The figure illustrates that the attacker had gained access to the internal network environment. Had the organization implemented another important layer of security, such as network access controls (NAC), the attacker would have likely only gained access to a secured guest network or attained no network access at all. Due to the absence of this important layer of security, in the form of network access controls, the attacker had attained access to the internal network environment i.e. “the soft chewy center”. The figure below illustrates the scenario.
The attacker also connected a “drop box” (as illustrated at the bottom right of the previous photo) to the network and hid it under the desk. The drop box is a small form factor computer with many penetration testing tools pre-installed and configured. The drop box also has the ability to tunnel out of the network and connect back to the DirectDefense penetration testing lab (assuming such outbound connections are allowed on perimeter firewalls). In this case outbound connections were indeed allowed enabling the drop box to “phone home” as they say. Once the outbound connection was established, the attacker then verified the ability to access the drop box remotely. This connection essentially allowed remote access to the internal network as if the attacker was still sitting in cubicle where the drop box was left.
The attacker then left the building and returned to the DirectDefense headquarters in Colorado. Utilizing the newly attained remote access to the internal network of ClientX, the attacker then proceeded to continue the penetration test remotely.
At this stage of the penetration test, DirectDefense identified another important layer of security that was absent. ClientX did not properly implement strong egress filtering at their perimeter firewalls. Egress firewall access controls are just as important as ingress firewall access controls, however many organizations do not realize this reality, and thus implement relaxed egress firewall access controls, or no egress firewall access controls at all. This vulnerability allowed outbound connections to be established from the very sensitive end-user network environment to anonymous systems outside their network (such as the DirectDefense penetration testing lab). The absence of this layer of security allowed the attack to continue successfully without detection by ClientX personnel. This vulnerability also eventually allowed the exfiltration of sensitive data from the ClientX network.
Another common security control that is absent in most organizations is proper internal network segmentation. Most organizations have a relatively flat network internally. Once you have connectivity to the internal network environment in any facility, you have access to the majority of their systems (from a network connectivity-level at least) regardless of the system’s geographic location or its data classification level. Rarely does an organization segment the internal network properly with internal firewall access controls. This was indeed the case in the scenario set forth in this article. ClientX did not properly segment the internal network environment. This vulnerability allowed the attacker to gain network-level access to systems in locations all over the globe. Had ClientX implemented proper internal network segmentation, the breach at the Springfield office would have been just that; a breach at the Springfield office. Instead, due to the lack of yet another layer of security, the breach was allowed to become a breach of their entire global network; a much bigger problem.
At risk of sounding cliché, we elicit the “soft, chewy center” concept one final time. Those of us that are in the business of penetration testing know that once you gain access to the internal network, it is only a matter of time before you find vulnerable systems, compromise those systems, then escalate privilege and begin to gain access to sensitive data. In this given scenario the DirectDefense consultant was able to quickly identify existing vulnerabilities within the internal network environment and quickly leverage the identified vulnerabilities to escalate privilege to Domain Administrator level. The majority of people reading this article probably know exactly what that means. For those of you who do not, this essentially implies that we have the keys to the kingdom. We have full access to essentially any domain-connected Windows system within the environment, and hence all the data it contains. As they say, “Game over”.
In conclusion, DirectDefense cannot emphasize enough the importance of the concept of Defense in Depth in the development of an organization’s security program. As it regards the scenario previously outlined, had the client fully embraced the concept of Defense in Depth in its security program, we believe the emulated attack would not have been nearly as successful, and the attacker would not have gained unauthorized access to sensitive data in such a short period of time. Those organizations who do not learn, and properly implement, this important concept will likely find themselves to be in the news, eventually, as the next big compromise.
If you’d like to test how well your organization has implemented the Defense in Depth strategy, please contact sales@directdefense.com to schedule an assessment.
Written by: Dean Meyer
Dean Meyer is a principal security consultant with the DirectDefense assessment practice with over fifteen years of combined experience in information technology and information security consulting. Dean provides a broad range of information security assessment and consulting expertise targeting various components of the enterprise environment (perimeter, enterprise, applications, etc.).
Prior to joining DirectDefense, Dean worked for Accuvant and Business Network Consulting (BNC). While there, he focused his efforts on security assessment and penetration testing work for a broad range of industries including finance and banking, legal, healthcare, e-Commerce, manufacturing and government entities. Dean’s experience also includes performing assessment and penetration testing to meet compliance requirements with industry standards such as PCI, HIPAA, NERC-CIP, FCA and others.
 Back
Back
