End-to-End Security Management Powered by Our SOC
The DirectDefense Security Operations Center Analyst Team uses ThreatAdvisor internally, which improves the speed, efficiency, and accuracy of our SOC. We leverage our own experience and knowledge base with ThreatAdvisor, inclusive of built-in workflows and playbooks, to ensure a repeatable, high standard of service while allowing for customization and flexibility for your specific needs.
We consider ThreatAdvisor to be one of the best SOAR platforms, as it delivers continuous, robust security monitoring and management, and its intuitive customer dashboard provides a clear view of remediation management tactics and how selected strategies are affecting your organization’s overall security.
Built from the Ground Up for Scalability
ThreatAdvisor integrates seamlessly with other solutions, so you always have a single interface for threat management, complete with in-depth data and clear context, allowing you to scale as your security and compliance needs evolve.
Vulnerability and asset data is collected and processed from several sources, giving you a complete view of your cybersecurity posture at all times, right from the ThreatAdvisor interface. And the benefits don’t stop there. ThreatAdvisor supports a host of security activities to ensure your organization is always a step ahead.
- Penetration Testing
- Operational Technology (OT) and Industrial Control Systems (ICS) Services
- Vulnerability Management
- Managed Detection & Response (MDR)
- Compliance Assessments
- Enterprise Risk Assessments
- And more
Security Areas Within the ThreatAdvisor Platform
As your partner, we manage the ThreatAdvisor platform to manage and monitor your organization’s security, all while providing you with customized outputs to help you stay on top of your cybersecurity posture and feel confident in our remediation tactics and security strategies.
Use Case
Penetration Testing
What We Manage:
- Import results from testing tools
- Curate security findings with evidence
- Create project report
- Generate status and comprehensive reports
- Perform and record retesting results
What You Get:
- Clearly view findings and evidence
- Easily access status and comprehensive reports
- Indicate when findings have been remediated
- Track and report on security trends
Managed Detection & Response
What We Manage:
- Monitor incoming security events
- Triage events to determine if investigation is required
- Manage detection cases for investigators
- Escalate investigations that become incidents
- Manage incident response
- Generate activity reports
What You Get:
- View detection cases of investigations and incidents
- Interact directly with our SOC on detection cases
- Assign detection case ownership
- Easily access reports of MDR activity
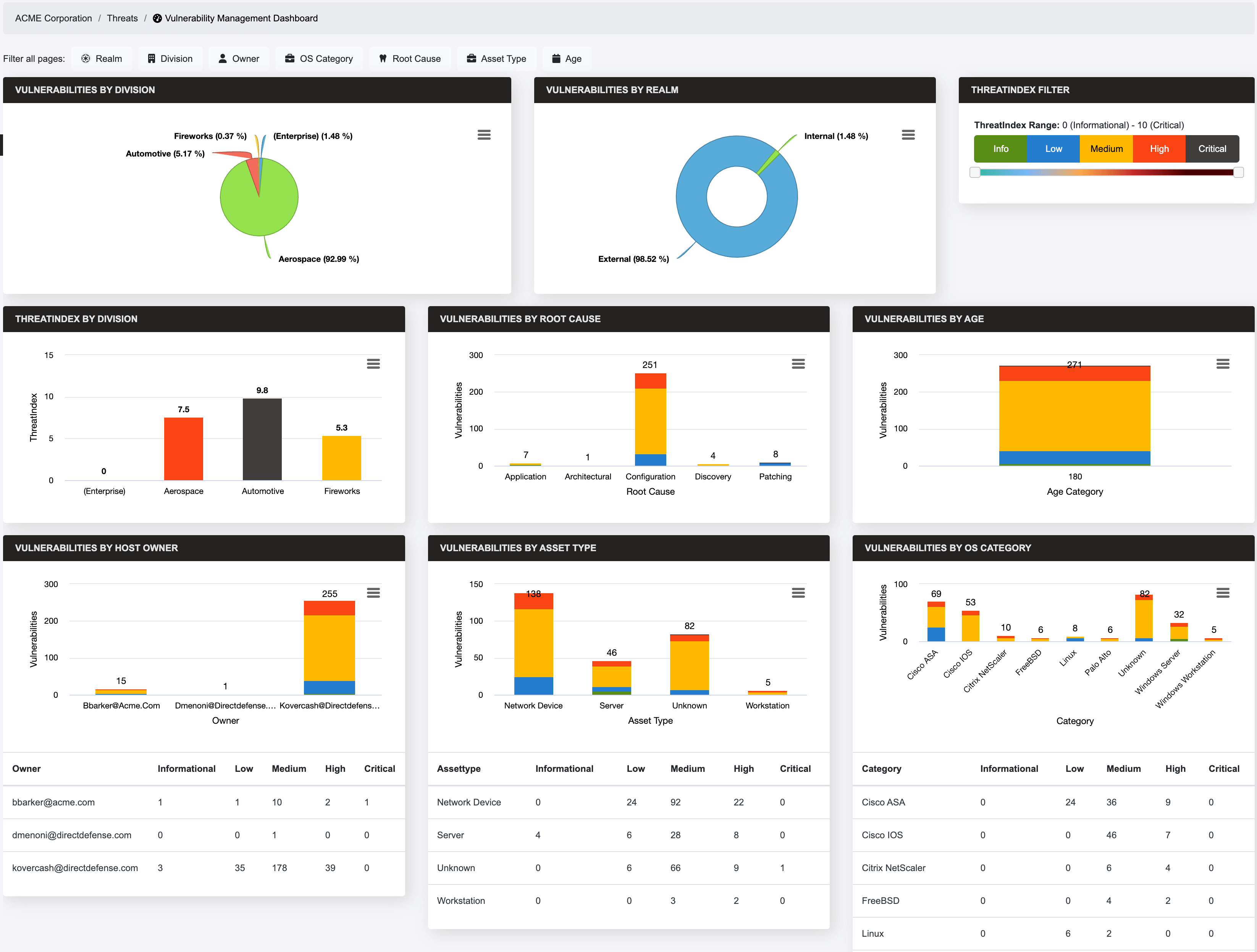
Vulnerability Management
What We Manage:
- Import security vulnerabilities from scanning tools
- Classify vulnerabilities by category and root cause
- Prioritize vulnerabilities
- Escalate detected vulnerabilities based on severity
- Generate reports showing vulnerability trends
What You Get:
- View detected vulnerabilities
- Respond to escalated vulnerabilities with remediation
- Access comprehensive and trending reports
- Identify vulnerability exceptions
Compliance
What We Manage:
- Perform and record results of compliance assessments for regulatory requirements
- Generate reports of compliance assessment
- Plan projects to reach specified levels of compliance through remediation selection
What You Get:
- View results of compliance assessments
- Generate reports of compliance assessments
- Plan projects to reach specified levels of compliance through remediation selection
Risk Register
What We Manage:
- Track security exceptions
What You Get:
- Enter policy and security exception requests
- Review, approve, or reject policy and security exception requests
- Assess and record the inherent, residual, and overall risk of an exception request
- Track, manage, and report all exception requests
Asset Management
What We Manage:
- Correlate and manage assets across all services
- Adjust priorities based on asset business value
- Determine asset owner and business unit
What You Get:
- Provide the business value of assets
- Organize assets by business unit
- Assign ownership to assets
- View overall security posture of an asset
How to Use ThreatAdvisor’s Key Features
ThreatAdvisor is designed intuitively so you can view, track, and export information when you need it. We have implemented several key features that deliver a comprehensive look at your security posture at any time – and provide actionable insights to help your organization stay protected.
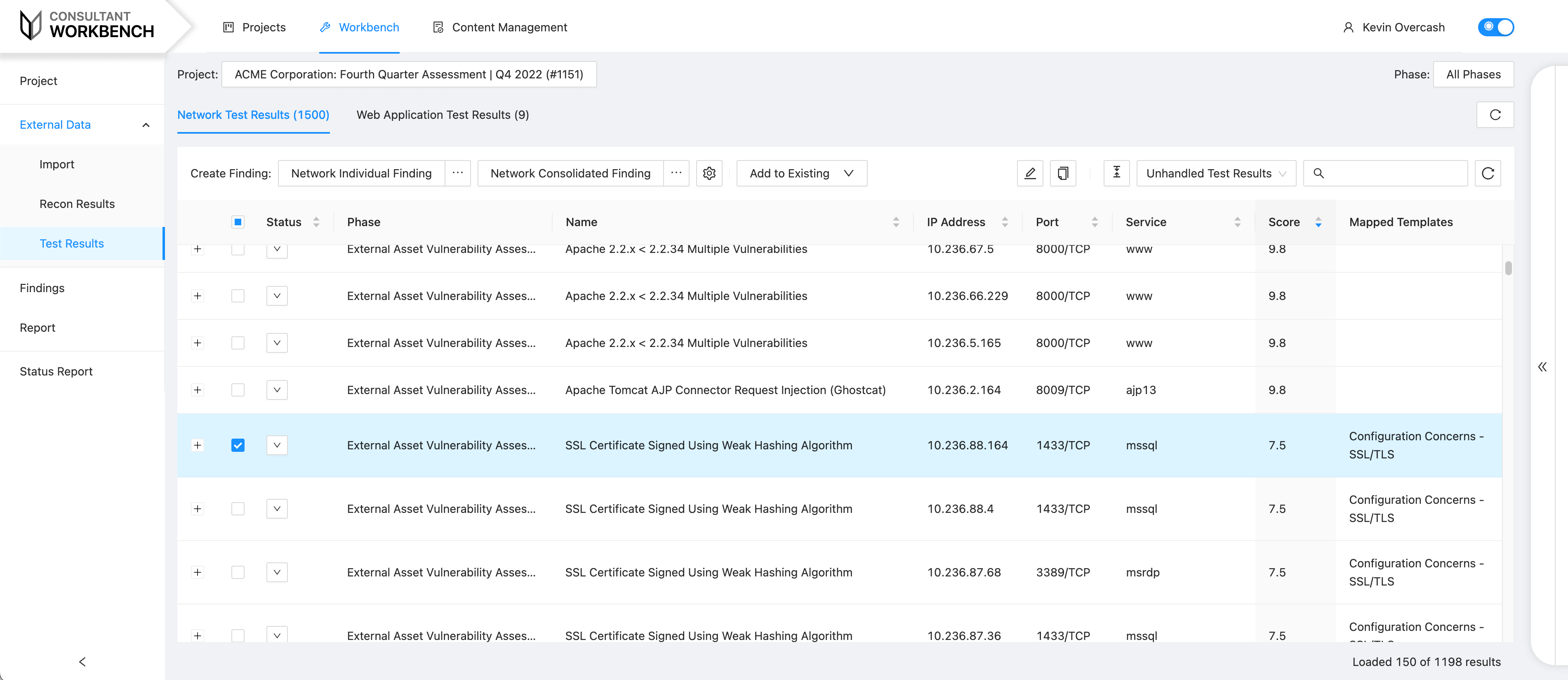
Consultant Workbench
Your DirectDefense consultant imports assessment results and creates findings directly from those results. This activity allows you to easily view findings, access status reports, track remediation progress and monitor security assessment trends. Through Consultant Workbench, your consultant can customize individual reporting sections for your organization using content from the knowledgebase.
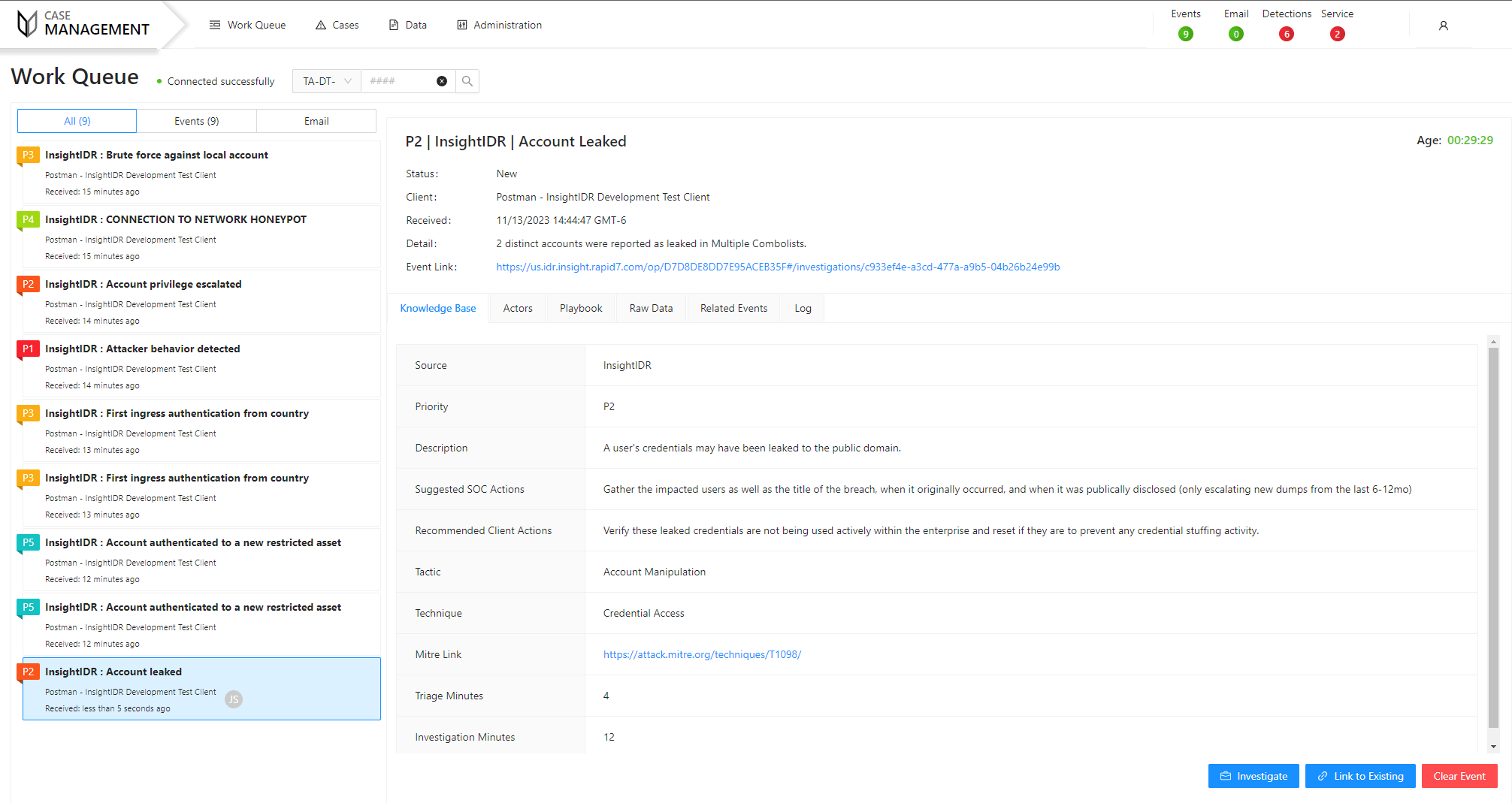
Case Management
View a work queue listing all incoming events and emails, as well as a knowledgebase for all types of security events. The knowledgebase includes event playbooks that detail automated and manual steps to investigate an event, and all events are investigated in detection cases with review timers to ensure they’re regularly monitored. All communication with your team is tracked in real-time within a detection case so nothing is overlooked.
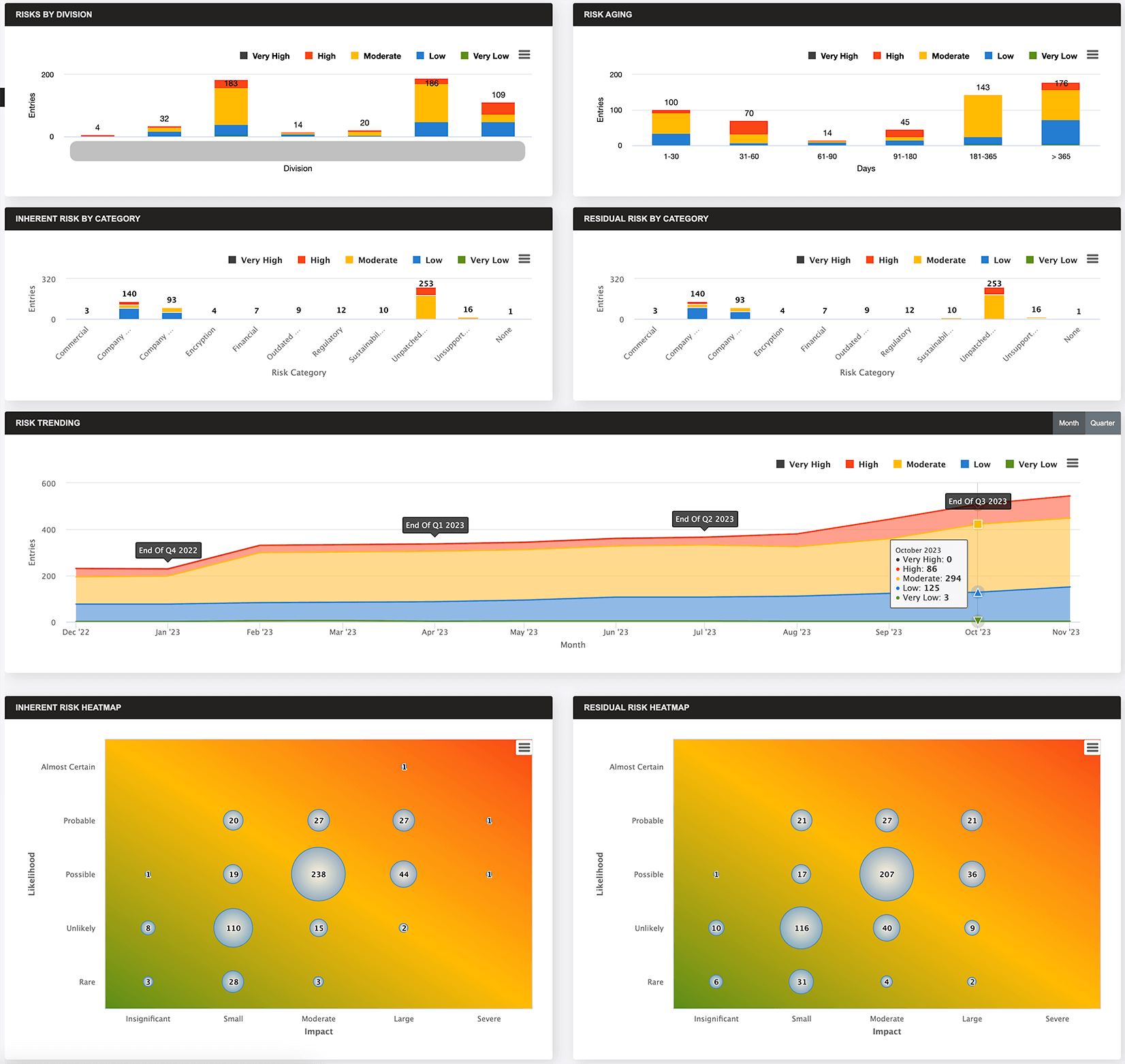
Risk Register
Turn here to manage policy and security risk exceptions using easy-to-navigate dashboards. New exception requests are either entered manually or come in through integrations with client ServiceNow instances and are either approved or rejected. All exception requests are categorized and evaluated for risk exposure and mitigating factors. You can easily track approvals through a multi-tiered system and assign higher-level approval requirements for exception requests as the overall risk exposure increases.
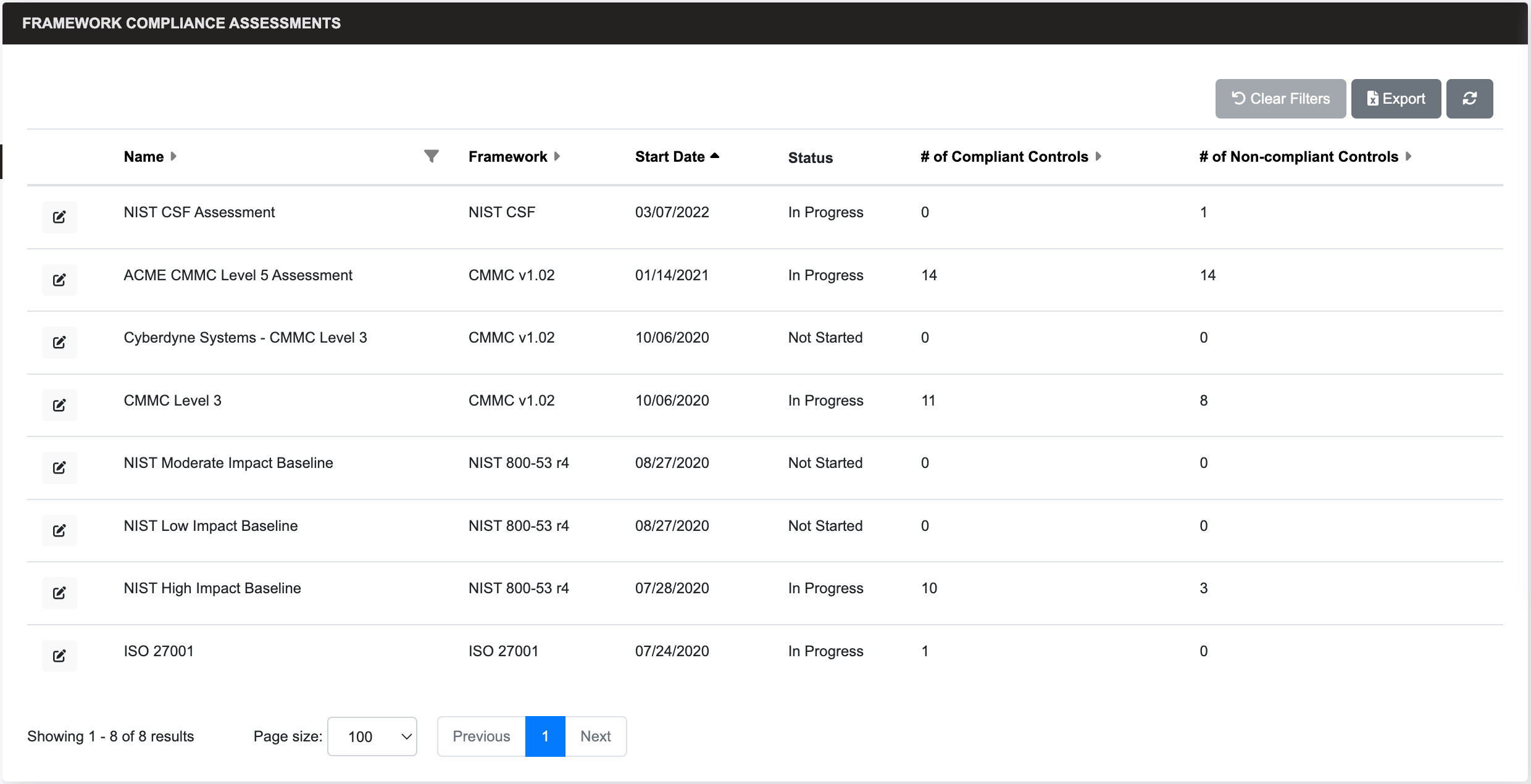
Compliance
View a framework of your compliance assessments and assessment details, and utilize Compliance Project Planning to select your desired level of compliance and remediations for non-compliant items to determine the time and cost of a compliance project. You can access the compliance knowledgebase of data collection procedures, notes, and potential evidence to gather for each control in all supported regulation frameworks.
Vulnerability Management
View easy-to-read dashboards to see all detected vulnerabilities, respond to escalated vulnerabilities with a remediation plan, access comprehensive and trending reports, and identify vulnerability exceptions.
Data Sources
ThreatAdvisor collects and processes vulnerability and asset data from several sources, and compiles them into a holistic view of your organization’s security posture.